Erion’s David Holder provides an insight into the recent IPv6 Security Workshop
I was privileged to be invited to speak at this year’s IPv6 Security Workshop arranged by the UK IPv6 Council. The event, held at the BT Centre in central London, was oversubscribed well in advanced with around 170 delegates registered. This was the largest subscription for any IPv6 Council event to date and the speediest registration yet! The speaker line-up included many leading IPv6 security experts, those involved in developing IPv6 security standards, the National Cyber Security Centre and a range of industry experts. We were all delighted to see such a high level of interest in IPv6.
In my introductory presentation, I gave a quick, but comprehensive, overview of the fundamentals of IPv6 Security. You can view the slide deck here. For those who were not able to attend, here are a few highlights.
IPv6 Security Fundamentals
The first crucial point to appreciate is that IPv6 is everywhere. It is the default on all major operating systems and is widely deployed across the Internet. Further, its growth is exponential and at the current rate all Internet users will be using IPv6 by 2020. If you have IPv6 today you will find that over 75% of your traffic will be carried by IPv6 rather than IPv4.
Even if you have not deployed IPv6 it is important to understand that most of current your networks areIPv6 ready and are IPv6 enabled by default. All modern operating systems contain IPv6 stacks. These are on by default. Operating systems will use IPv6 if they possibly can. This means two things: firstly the majority of security vulnerabilities associated with IPv6 are on your networks today even if you have not deployed IPv6 and secondly if you look on your networks you will see IPv6 traffic. Therefore it is essential that you implement IPv6 security, ideally you should have done this over decade ago when IPv6 was already widely implemented in common operating systems. It is not sufficient to, as some suggest, turn off IPv6. Partly because modern operating systems are IPv6 operating systems and also because turning off IPv6 is often an unsupported configuration.
There are two, possibly three, widely held misconceptions regarding IPv6 and IPv6 security. The first two are:
Misconception 1: IPv6 is more secure than IPv4
Misconception 2: IPv6 is less secure than IPv4
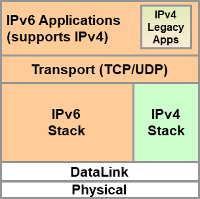 Both of these are wrong. They both assume that a comparison between IPv4 and IPv6 is meaningful, it isn’t. The reason is simple, in our networks there are no IPv4 stacks, all stacks are IPv6 stacks. Therefore, whether you are using IPv6 or not the vulnerability surface of your IPv4 network is practically identical to that of an IPv6 network. There is a combined vulnerability surface consisting of IPv4 and IPv6 vulnerabilities. Comparing the two is therefore meaningless.
Both of these are wrong. They both assume that a comparison between IPv4 and IPv6 is meaningful, it isn’t. The reason is simple, in our networks there are no IPv4 stacks, all stacks are IPv6 stacks. Therefore, whether you are using IPv6 or not the vulnerability surface of your IPv4 network is practically identical to that of an IPv6 network. There is a combined vulnerability surface consisting of IPv4 and IPv6 vulnerabilities. Comparing the two is therefore meaningless.
There is another major misconception that is relevant to IPv6 security and that is,
Misconception 3: IPv6 is IPv4 with longer addresses
It isn’t. IPv6 has many complex and subtle differences from IPv4. It is a new protocol with many new features. Even in those areas that are superficially the same as IPv4 there are surprising differences. As a result what is often best practice in IPv4 is not best practice in IPv6.
Even IPv6 and IPv4 addresses are very different and not just in their length. For example:
- NEW New attributes: length, scope and lifetimes
- NEW It is normal for IPv6 interfaces to have multiple addresses
- NEW IPv6 addresses can change over time
- DIFFERENT Multicast is very important in IPv6
- NEW There are large numbers of methods for assigning interface identifiers
- DIFFERENT How addresses are used and managed are different
- DIFFERENT Global public addresses are the norm
- NEW And of course there are a huge number of addresses
These differences and that includes all the differences not just those relating to addresses, have a direct impact on the IPv6 vulnerability surface and the mitigation techniques required for IPv6.
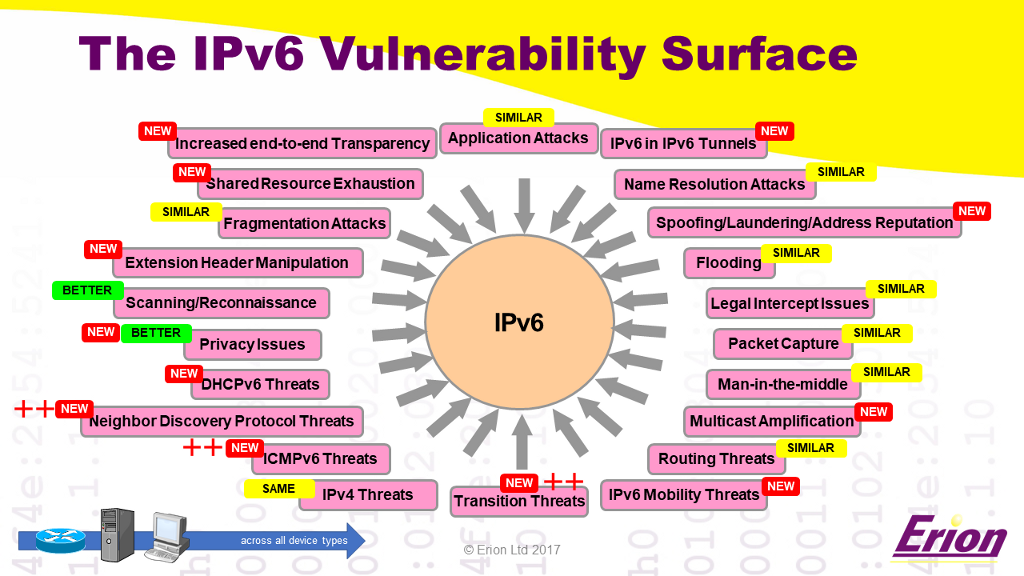
Whilst it is not possible to list all the IPv6 vulnerabilities it useful to get an idea of where the problems lie. The slide below shows a rough approximation of the IPv6 vulnerability surface. It is not complete and it cannot show how probable or how significant each of the risks is. What it does show is how many new and different areas there are that need to be considered when implementing IPv6 security.
In the presentation, I went through a number of key areas to illustrate three things; first that IPv6 is significantly different from IPv4, second that some of the areas of vulnerability shown in the above diagram contain many vulnerabilities themselves and finally that not everything is worse. Some things are better than IPv4. Of particular note is the area of scanning and reconnaissance. In IPv4, scanning a whole network is simple and fast. In IPv6, it is impractical to directly scan every address in an IPv6 subnet. This is because testing every address in an IPv6 subnet would take hundreds of thousands of years even on Gigabit networks. This is not to say that attackers cannot discover the addresses of IPv6 nodes, they can, it is just much more difficult for them to do so. However, do not forget that all of the vulnerabilities of IPv4 exist in the IPv6 dual stack, therefore even though scanning IPv6 might be difficult if nodes also have IPv4 addresses is it is still trivial for an attacker to find those nodes from their IPv4 addresses.
When designing and implementing your IPv6 security policy you should pay particular attention to these areas that are listed as new in the diagram. Those areas that are similar to IPv4 are often mitigated in IPv6 using the same techniques that are common in IPv4. Therefore, you should begin by ensuring that the security techniques that you use for IPv4 are also implemented for IPv6. For example, you should use ingres and egress filtering in both IPv4 and IPv6 and you should use unicast reverse path forwarding in both.
In terms of the many differences in IPv6, you need to pay particular attention to the NEW areas in the diagram. Of these, the increased end-to-end transparency, extension header attacks, neighbor discovery attacks and transition mechanism attacks are of particular importance, but this is not to say that you can ignore the other areas. In the presentation I went through each of these and gave specific examples of the types of vulnerabilities. Here are five of the areas that I covered:
- End-to-end Transparency - Public addresses are the norm, there is no NAT44. Firewalls are necessary (as they are with IPv4).
- ICMPv6 - Much more complex and critical then ICMPv4. Requires more complex security techniques.
- Extension Header Manipulation - Whilst the IPv6 header is simple, extension headers that carry options are extremely complex and can be used by attackers in a variety of ways even to hide attacks from security devices.
- Neighbor Discovery Protocol - NDP is very important to the operation of IPv6 it is also complex. It introduces a number of vulnerabilities to IPv6 nodes and subnets. Securing against these is especially important.
- Transition Mechanisms - The huge number and complexity of transition mechanisms in itself increases the vulnerability surface. Worse, these create complex interactions between IPv4 and IPv6 and some are standard on many operating systems. Mechanisms such as Teredo are designed to tunnel through IPv4 NAT and firewalls raising the possibility of Teredo being used to circumvent perimeter security.
I then gave a whirlwind tour of IPv6 security features and their pros and cons. Briefly these were:
- IPsec - Largely the same as IPsec in IPv4. The one key difference is how it is used. The absence of NAT44 in IPv6 makes IPsec transport mode more practical than in IPv4 changing the way IPsec is used.
- Privacy Addresse - Useful (and the default on many platforms). The temporary nature of privacy addresses has significant implications for operational management including IPv6 Forensics, audit and legal intercept
- Opaque Static Addresses - Useful (and becoming the default). Avoids linking IPv6 addresses to hardware addresses.
- SeND and CGAs -Secure Neighbor Discovery (SeND) and Cryptographically Generation Addresses (CGAs) are not widely implement in many operating systems.
- RA-Guard - Extremely useful protection against rogue IPv6 routers, but can be circumvented using extension headers.
- DHCPv6-Shield- Extremely useful protection against rogue DHCPv6 servers, but can be circumvented using extension headers.
- Neighbor Discovery Inspection- Extremely useful protection against attacks against Neighbor Disocvery, but can be circumvented using extension headers.
- MLD Snooping- Useful for limiting the effectiveness of multicast attacks. Primary use is to improve LAN multicast performance.
I finished by suggesting that the real security benefits of IPv6 will only be seen when we get rid of IPv4 and move to IPv6-only networks. Indeed, some organisations are already moving to IPv6-only networks mainly for operational and cost reasons. Moving to IPv6-only networks will also have security benefits. Removing all of the IPv4 and transition mechanism vulnerabilities it will be possible to make full use of the security features of IPv6.
The key high-level points to take away from my presentation were:
- IPv4-only networks are historic, they rarely exist today
- IPv6 should already form a part of your security policy today
- IPv6 has introduced many new vulnerabilities and features
- IPv6-only networks will have fewer vulnerabilities
- Legacy IPv4 thinking is a security risk - staff IPv6 competency is crucial
Erion IPv6 Cyber Security Training
Erion is the world’s leading IPv6 training company with the largest portfolio of IPv6 training courses covering all topics and environments. We have a range of IPv6 security training courses from short introductions to advanced and detailed technical IPv6 security courses. Further information on our IPv6 training can be found at www.ipv6training.com.
Erion recently released a NEW IPv6 Forensics course. This advanced course covers all aspects of IPv6 forensics and is ideal for all those involved in forensic activities.
Other Presentations from the IPv6 Security Work Shop
You can find many of the other presentation from the workshop at http://www.ipv6.org.uk/2017/03/31/ipv6-security-workshop-jul-2017/.
This entry was posted on Saturday, July 22nd, 2017 at 2:53 pm and is filed under IPv6, Security, News, Conference. You can follow any responses to this entry through the RSS 2.0 feed. Responses are currently closed, but you can trackback from your own site.